Your network needs to support your digital transformation, and you’re likely evaluating a number of technology upgrades. But what’s the “right” technology to consider?
The answer: It depends.
Your business has its roadmap, its goals, and a pretty clear picture of its future success. You might be evaluating:
- How to improve your customer’s digital experience
- How to enhance network security for your distributed workforce
- How to increase your IT staff productivity
- How to make sense of your disconnected network data points
Networks are more than just connectivity now…. they’re smart. Network technologies like SD-WAN, SASE, AIOps, and others work on top of your network to ensure the best customer experience. However, each technology has a sweet spot of support, and you’ll likely see elements of several technologies that, when combined, will provide the ideal combination that’s right for your business.
Let’s dive in.
AIOps (Artificial Intelligence for IT Operations)
Network monitoring happens everywhere but usually provides only “circuit’s up” or “circuit’s down” information. AIOps is a technology that allows us to go way beyond “red light / green light” monitoring by using artificial intelligence and machine learning to analyze and automate IT operations. Companies in various industries can use AIOps to detect and resolve IT issues quickly and proactively.
Imagine if your network can provide you the information you need to fix it. AIOps lends the needed intelligence to correlate multiple data points from lots of different systems that may not have excellent linear relationships, and provides you with a plan to fix whatever may be broken.
Here’s a simple example that illustrates the differences between monitoring, monitoring with a single pane of glass, and observability with AIOps (if cars were so equipped):

Monitoring provides a data point for a single item without additional content.
“Here’s your tire pressure.”
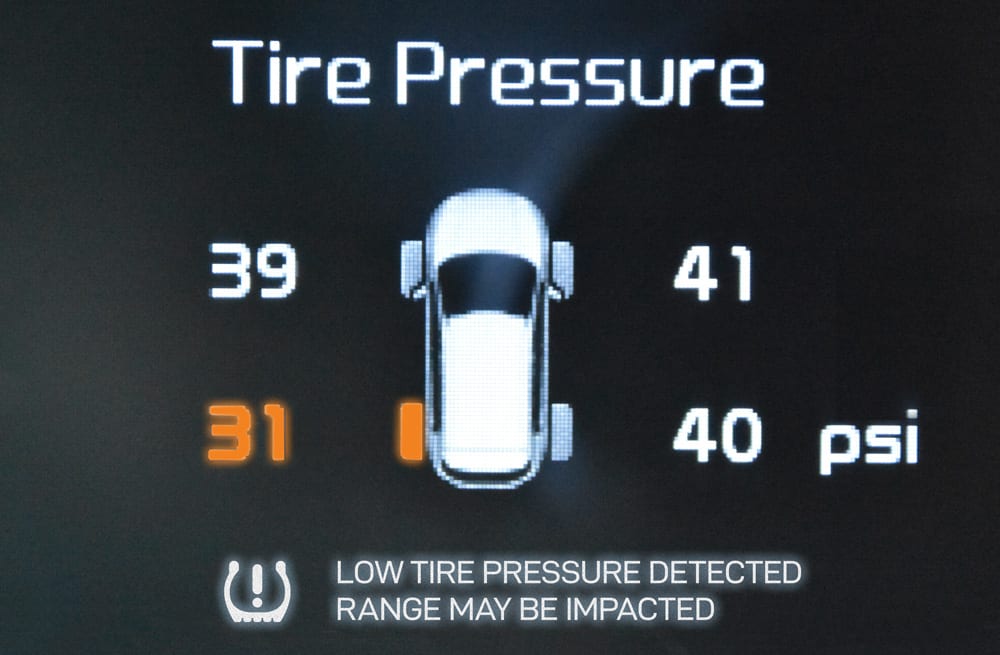
A Single Pane of Glass provides multiple data points in content, but without insight.
“Here’s your tire pressure compared with the pressure of all other tires.”
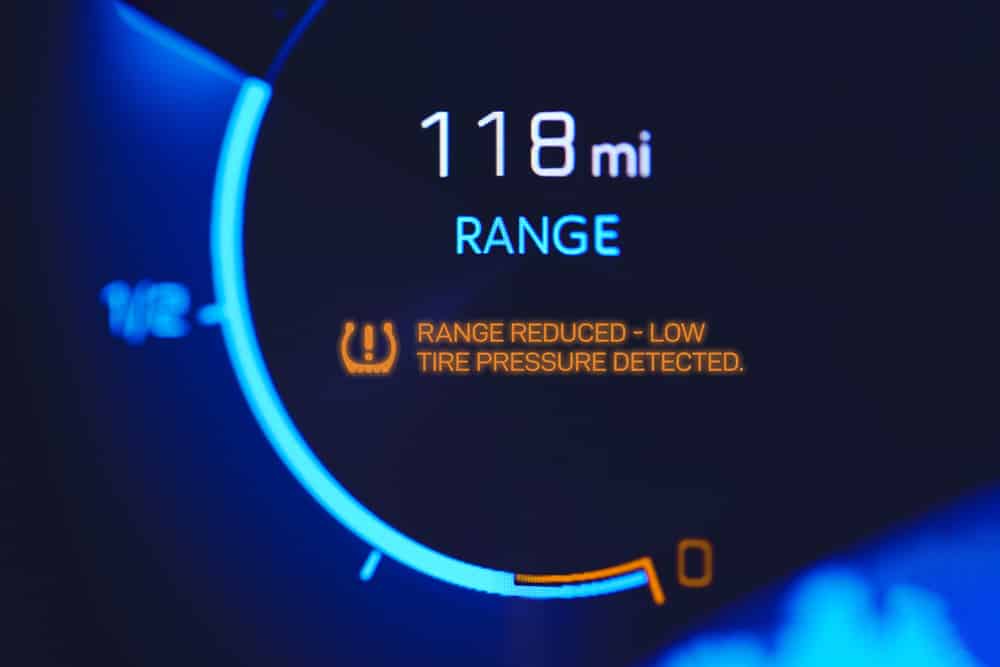
Observability with AIOps looks across silos and domains for the actionable insights needed.
“Your gas mileage is suffering because your rear driver side tire pressure is low.”
Here’s a network example: Within a network with AIOps, if a vendor has opened a change ticket to perform maintenance on the network, the system learns that corresponding outages can be temporarily ignored, since it understands that the change the vendor is making to the network is actually causing the outages – breaking something to fix something. In this case, the change ticket is a “known cause” of the outage. If there’s no change ticket open, then AIOps understands that the outages are now abnormal, have no known cause, and need to be acted upon.
Who might use AIOps?
A bank can adopt AIOps to monitor its customers’ transactions, and correlate data to detect fraud and prevent financial losses. Similarly, a healthcare provider can use AIOps to monitor patients’ vital signs and detect abnormalities based on known causes (such as the correlation that a particular abnormality is caused by the chemotherapy the patient is currently receiving, and is therefore currently normal), enabling the healthcare provider to intervene promptly, and appropriately.
When companies adopt AIOps, the data created requires a similarly intelligent approach in those companies’ networks. If you’re running a lot of cloud services, AIOps in your network becomes very powerful. AIOps takes many data points and starts to make sense of the “noise” created, diagnosing issues so that you can take action with confidence.
Who might not use AIOps?
AIOps may not be a solution every business needs in their networking environment. For instance, small businesses may not have complex IT operations that require AIOps. Additionally, point-of-sale only locations that need robust performance (a network that stays up), but do not need a lot of data analysis, may not find AIOps necessary in their networks.
Finally, if your network portal or network management system provides the diagnostic information you need without lengthy analysis – the detail provided by AIOps may not be needed to ensure continued sound network operation.
SD-WAN (Software-Defined Wide Area Network)
Chances are, you’ve started evaluating how SD-WAN fits within your networking ecosystem. To review, SD-WAN is a technology that uses software to manage and optimize wide area networks (WANs) rather than relying on traditional hardware-based WANs. It provides a software management layer for your network equipment (such as routers and switches), and for all of the disparate vendors you purchase from.
Who might use SD-WAN?
SD-WAN certainly has a place in your infrastructure if your company has many brick & mortar locations, with remote sites connected only with a broadband link (think: multi-site enterprises, retail, banking, healthcare). If your company fits this profile, there’s a good chance that the addition of an SD-WAN overlay to your network will improve its security, performance, and operational costs. SD-WAN shines in optimizing the throughput of lower speed data connections.
Retail might use SD-WAN to, for example, optimize the buying experience by ensuring that store locations’ broadband connections are reliable and secure, providing the same “flagship experience” to customers visiting even the most remote stores.
Banks can use SD-WAN to improve branch connectivity by providing employees with secure and reliable access to the bank’s applications and data. You can accomplish the same ends (increasing security and throughput) using a private, dedicated last-mile access without the SD-WAN overlay capabilities – but it wouldn’t perform as well and it would cost much more.
Who might not use SD-WAN?
SD-WAN may not be ideal for all companies. Small businesses and single-site businesses have little need for a complex WAN, and therefore little need for the capabilities of SD-WAN. If your applications run on-site, and network connectivity is not key to operating your business, performance of those applications may not be enhanced by the addition of the software layer provided by SD-WAN.
If your networking is centralized in a data center and connected with big bandwidth pipes, you wouldn’t need SD-WAN because SD-WAN’s value is bringing performance and security to the lower throughput circuits connecting multiple offices. Traditional software defined networking (SDN) works best when orchestrating intra-data center networks. However – SD-WAN makes good sense when connecting multiple data centers across cities or countries together with your branch locations to optimize how data flows.
We also recognize that while government, banking, and healthcare organizations have the organizational structure to benefit from SD-WAN, regulatory compliance and rigid definitions of network technologies during procurement often force the choice of non-software-defined solutions, and cement traditional WANs for these industries.
SD-WAN breaks a traditional network mold; it’s not a circuit, but rather software on top of a WAN. The molded procurement choices in industries such as government, finance, and healthcare need to break too – but we trust that this change will eventually occur.
SDN (Software-Defined Networking)
SDN and SD-WAN are both networking technologies that leverage software to manage and optimize network traffic flows. The two services offer distinct functionality.
From a technical standpoint, SDN is a networking architecture that separates the control plane (which manages the network) from the data plane (which forwards network traffic). This separation allows companies to centralize network management, program network policies, and increase network flexibility and scalability. SDN is ideally applied to LANs (Local Area Networks).
SD-WAN, on the other hand, is a type of SDN whose goal is to optimize application performance for branch office and remote users across a WAN, even when underlying connectivity is not reliable. It makes an especially dramatic difference when the WAN connections are less expensive broadband – allowing customers to save money while ensuring great performance for even their most remote offices.
SDN provides network administrators with more fine-grained control over network policies and resources, while SD-WAN provides end-users with faster and more reliable access to their applications.
Who might use SDN?
SDN is an ideal technology for intra-data center networking. Data center operators use SDN for their day-to-day operations, such as door-access control or data configuration. If a manufacturer or a logistics company wanted to improve supply chain management by automating its inventory tracking and dispatching from a single location, SDN would work well.
Who might not use SDN?
Large businesses with a complex and geographically dispersed WAN might instead turn directly to SD-WAN to improve the WAN’s performance and resiliency. Additionally, companies that do not require network automation may not find SDN necessary in their networks.
SASE (Secure Access Service Edge)
SASE is a technology that combines network security and cloud-based connectivity into a single service – though each element can also be purchased individually, allowing companies the flexibility to build upon their security capabilities piece by piece.
Most companies have a VPN, and for some it may be good enough. But once employees work from home, from coffee shops, from vacation spots, ensuring security can mean compromising network performance. To improve performance you may turn to SD-WAN functionality. But if you’re only concerned about securing the networking of remote workers, the security pillars of SASE ensure security no matter where employees are.
SASE’s security pillars are SWG, CASB, FWaaS, and ZTNA, discussed further below. The SASE solution leverages the Cloud, so there’s no need to purchase new hardware. Plus, it’s managed by your vendor. This means that there’s no need to hire specialized security or IT staff to manage it.
SASE’s security elements are:
- Firewall-as-a-Service (FWaaS)
Firewall-as-a-Service, also known as cloud firewall, places the management burden of your firewall on your vendor. FWaaS delivers firewall functionality as a cloud-based service. SASE offers FWaaS as part of a unified, cloud-based security model.
- Zero Trust Network Access (ZTNA)
ZTNA, another component of a SASE solution, is an ideal security approach for your distributed employee environment. ZTNA requires that users first authenticate through a gateway to gain access to an application. This authentication occurs no matter where the user is located, no matter the device or network access they’re using. ZTNA focuses on policy, identity and content. The policies follow the identity of each user wherever they are, inside or outside the corporate perimeter. ZTNA is zero trust – meaning that no access is permitted until you say it is.
- Cloud Access Security Broker (CASB)
CASB is another essential security component of SASE. It secures traffic between an enterprise and its cloud providers. CASB comprises data security, threat protection, data loss prevention, and application control. And, crucially, it includes pre-configured “check-box” for government compliance.
CASB provides the visibility that helps you understand which software apps are being used and where sensitive data is going, no matter where users are located.
- Secure Web Gateway (SWG)
For many organizations, SWG fixes the limitations of web filtering. SWG includes a comprehensive web security solution. This includes SSL Proxy, URL Filtering, Intrusion Detection and Prevention (IDS/IPS), NextGen Anit-Virus (NG-AV), Data Loss Prevention, and Advanced Threat Protection. This package provides complete visibility and control over traffic, regardless of employee locations. As you grow, your SWG automatically scales to continue supporting you.
While these four security services form the minimal base package of SASE, your SASE vendor may offer more. This could include DNS security, browser isolation, and others. SASE is a means to control your policies and visibility into their enforcement, without an army of IT and security experts.
Who might use SASE?
SASE is ideal for large multi-site companies who are comfortable with cloud-based security, who need a managed solution to protect their remote and hybrid employees and their networks from cyberthreats, and who want to prevent access to inappropriate or malicious websites. Because SASE includes a full family of security products, companies use it for URL filtering, malware protection, content inspection, and enforcing their internal acceptable use policies.
For example, a retail company can use SASE to monitor its employees’ access to the company’s inventory management system, from anywhere, while still preventing data theft. Financial entities concerned about data loss can use managed security services so they can stop replicating all data to their own private cloud.
Who might not use SASE?
Some smaller businesses with simpler networks, in-office employees, and uncomplicated IT infrastructure may not need SASE security. Companies that do not handle sensitive data may not find SASE necessary in their networks. Companies most comfortable with on-premises solutions would naturally not consider a cloud-based solution like SASE.
Beyond the “Right” Technology – the Right Partner
Zayo’s value? We’ll help you figure this out. How much of any technology do you want to manage yourself? Do you feel as if you’re relinquishing too much control to your vendor when you consider the changes managed services bring? And where does private networking, IP VPN, dark fiber, wavelengths and other technologies fit into your plans?
How does all this technology come together best for your business? Understanding that requires a partner who can guide you, to ensure that you’re not wasting your time building a solution in isolation.

